Tech note: Connecting to an Amazon RDS database from a legacy EC2 server
Amazon’s Relational Database Service (RDS) is an excellent way to host databases. The service is affordable, low-maintenance, and self-contained. If you use the Amazon cloud, there are precious few reasons to maintain your own database server.
At some point, Amazon started requiring RDS instances to use Virtual Private Cloud (VPC) networking. However, if you’re like the NPR Visuals team, you might have older Amazon Elastic Cloud Compute (EC2) server instances that don’t use VPC but need to connect to RDS databases. Even if you don’t, you might need to connect to your RDS instance locally.
As is often the case with Amazon, it’s not entirely clear how to configure the correct security rules to allow access from outside the VPC. Here’s what worked for us.
During creation, make sure your RDS instance is publicly accessible. This setting cannot be edited later.
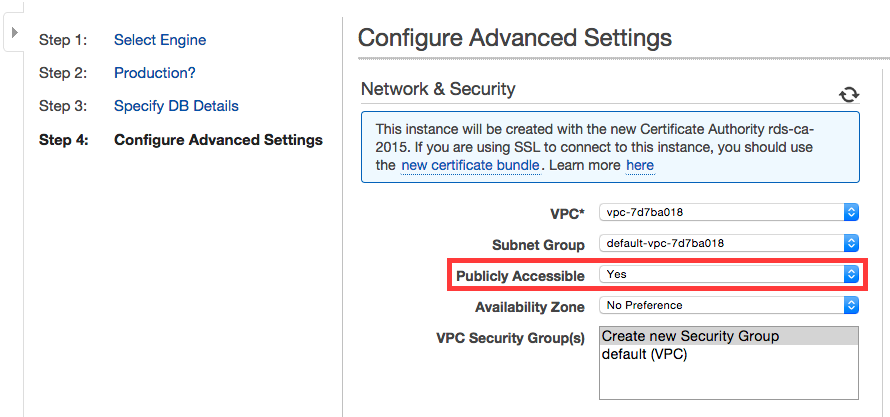
For the security group setting, either option will suffice, though creating a new security group will help isolate the network access rules for this database instance.
Once created, click on the security group from the instance details:
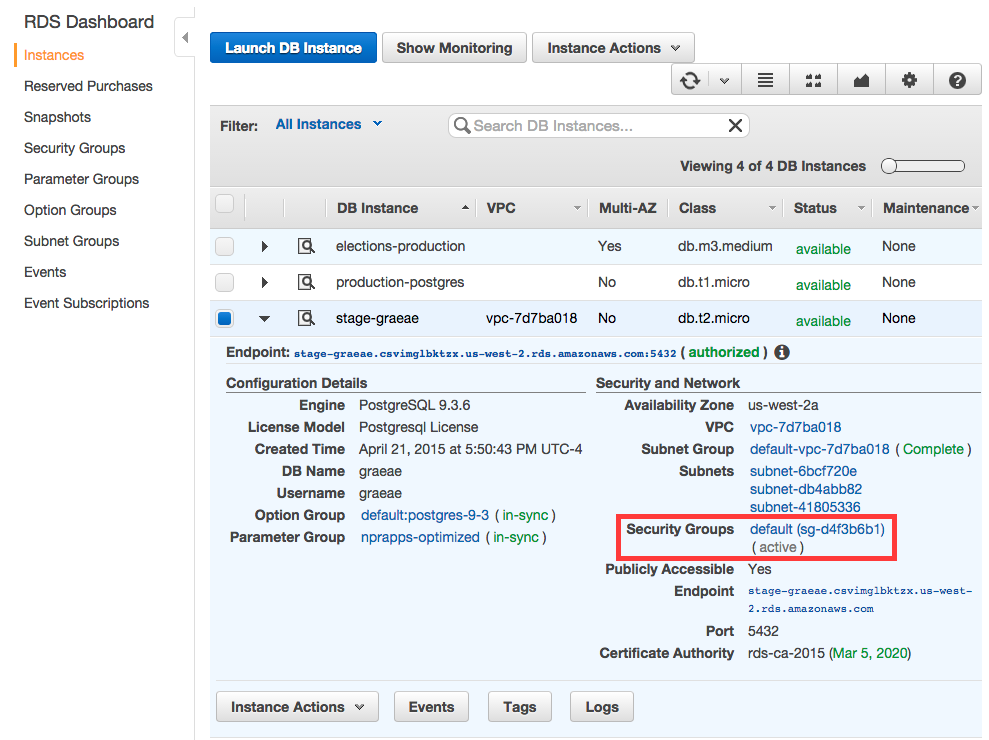
A new tab or window will open with the security group selected. Click the “Inbound” tab in the lower window pane, then click the “Edit” button to add rules to allow the IP addresses you want to access the RDS instance
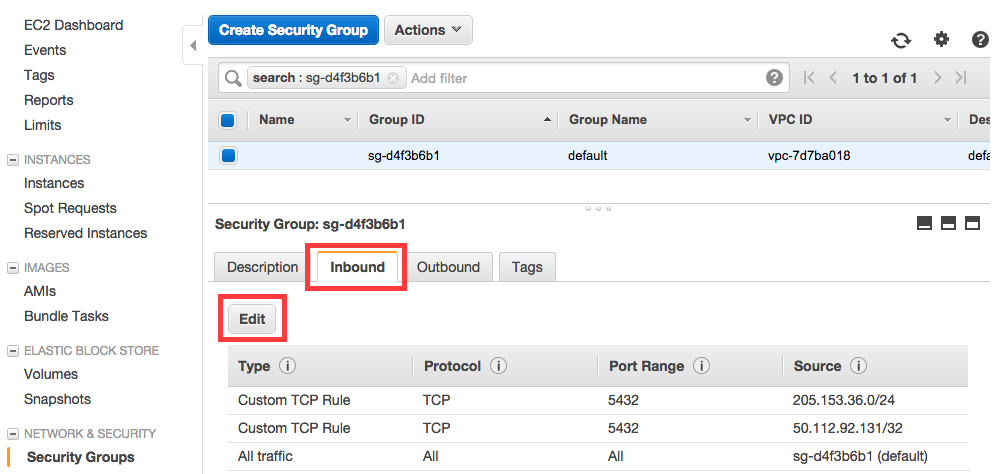
Now you can configure the inbound rules in the modal that opens:
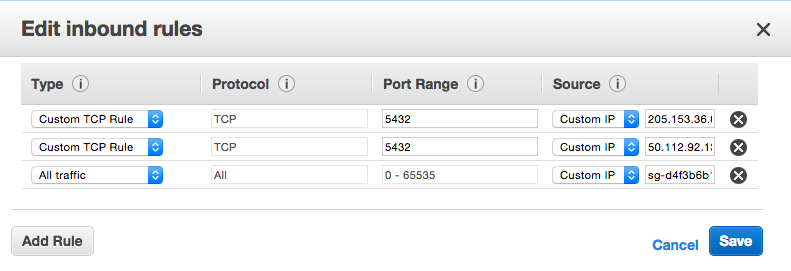
I found a lot of places in the VPC interface to set inbound rules, but only the security group rules actually worked to allow local machines and non-VPC EC2 instances access to the RDS database.
If you know a better way to handle this, let us know in the comments!
 visuals + editorial graphics
visuals + editorial graphics